- Home
- Essential Eight Cybersecurity Strategies
- Application Control
Application Control
What is Application Control and how does it work?
Each day thousands of malicious files and scripts are created with criminal intent. These files are created by bad actors to cause damage to organisations and are designed to bypass traditional security measures such as Antivirus.
Application control (Whitelisting) is a technique used by organisations to only allow the execution of known and trusted applications that have been approved by the organisation. Because malicious files have not been approved to run, Application Control is a very effective way of blocking the execution of malicious scripts within a target organisation.
The tools and techniques used to implement Application Control are varied and are dependent on each organisation’s specific business needs.

Why is Application Control so important?
The purpose of Application Control is to create multiple layers of security to make it increasingly difficult for bad actors to run malicious code in a target organisation. If one layer is breached, multiple security measures remain to protect the organisation’s computer systems.
Traditional Antivirus software cannot block applications when they encounter new, unknown malware, especially in cases where an organisation is being targeted by a sophisticated bad actor.
Application Control protects against unknown malware by only allowing known and trusted applications and scripts to run within the organisation.
Introspectus Key Features
What's the solution?
Introspectus helps organisations to maintain control over the IT security of their business environment. Introspectus does this by testing the effectiveness of the organisation’s Application Control policies on all endpoints daily.
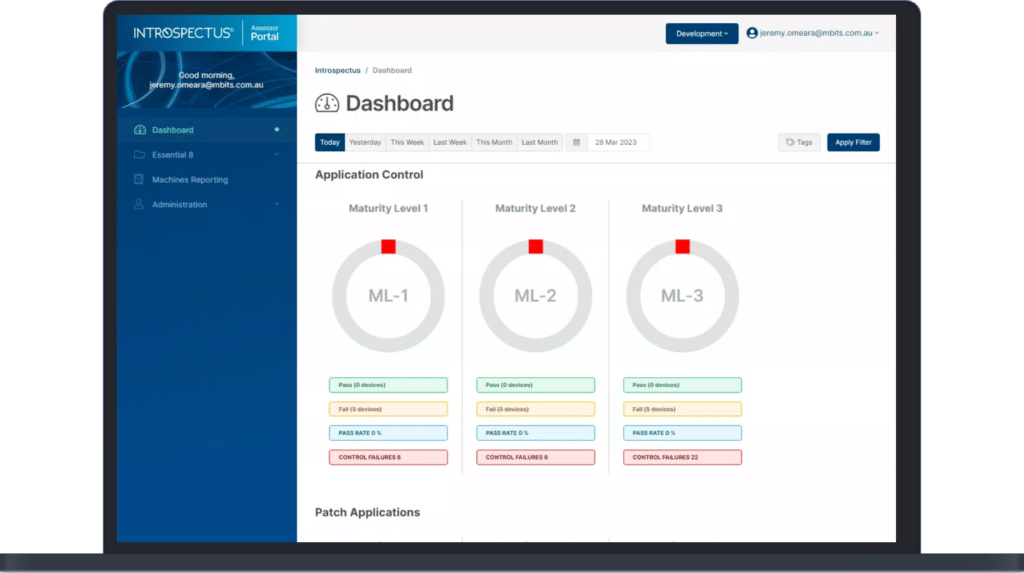
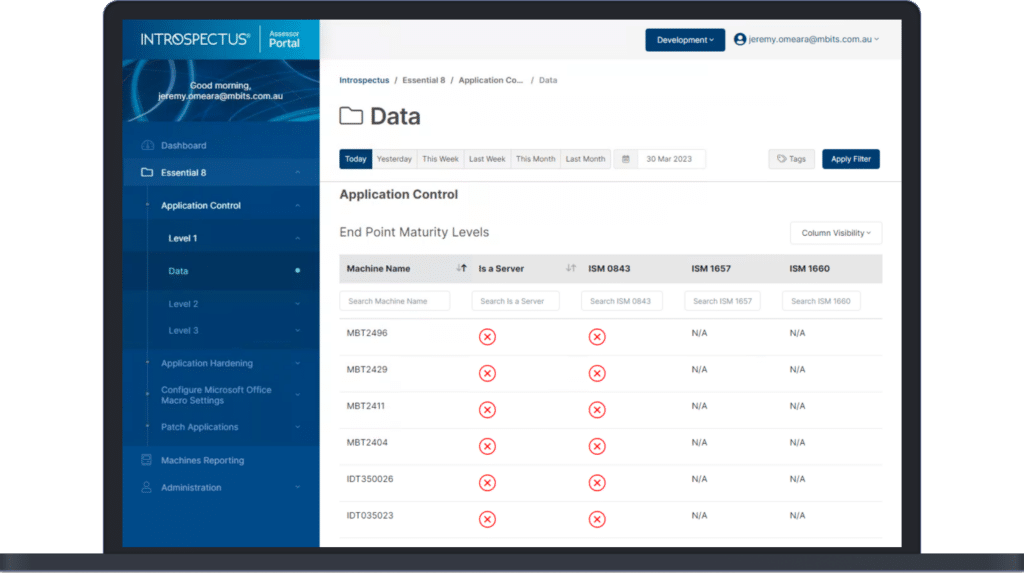
Introspectus confirms the effectiveness of an organisation’s Application Control by running tests for executables, software libraries, scripts, and installers (including hash-based) and producing a maturity score against ACSC’s Essential Eight Maturity Model.
Introspectus generates real-time reports on the Maturity Level of an organisation’s Application Controls, the information found, and any possible threats to user accounts.
Automated Daily Tests
Introspectus performs over 60 tests on each endpoint every day to provide organisations with confidence that their Application Control policies are effective.
Device Audit Report
Introspectus reports confirm that Application Control is deployed to each endpoint and identifies any endpoints where the policies have not been implemented.
Real-Time Reporting
Introspectus lets organisations confidently report to their management/board that they are continuously protecting all devices.