- Home
- Essential Eight Cybersecurity Strategies
- User Application Hardening
User Application Hardening
What is User Application Hardening and how does it work?
Each day thousands of malicious files and scripts are created with malicious intent. These files are created by bad actors to cause damage to organisations and are designed to bypass traditional security measures such as Antivirus.
User Application Hardening is an activity undertaken by organisations to configure applications used by individuals to ensure that applications work correctly and securely within an organisation. User Application Hardening limits an application’s ability to be used in an unintended manner to compromise a system’s security
The tools and techniques used to implement User Application Hardening are varied and are dependent on each organisation’s specific business needs and the applications used by the organisations.
Bad actors use Microsoft files with embedded Macros as part of phishing emails targeting users within an organisation. When a user opens the file, the Macro executes, performing malicious activity. This technique is one of the most prolific ways of compromising an organisation’s network and has a very high success rate.
It is difficult for anti-virus software to determine which Macros are malicious; as the software may be behaving as designed.
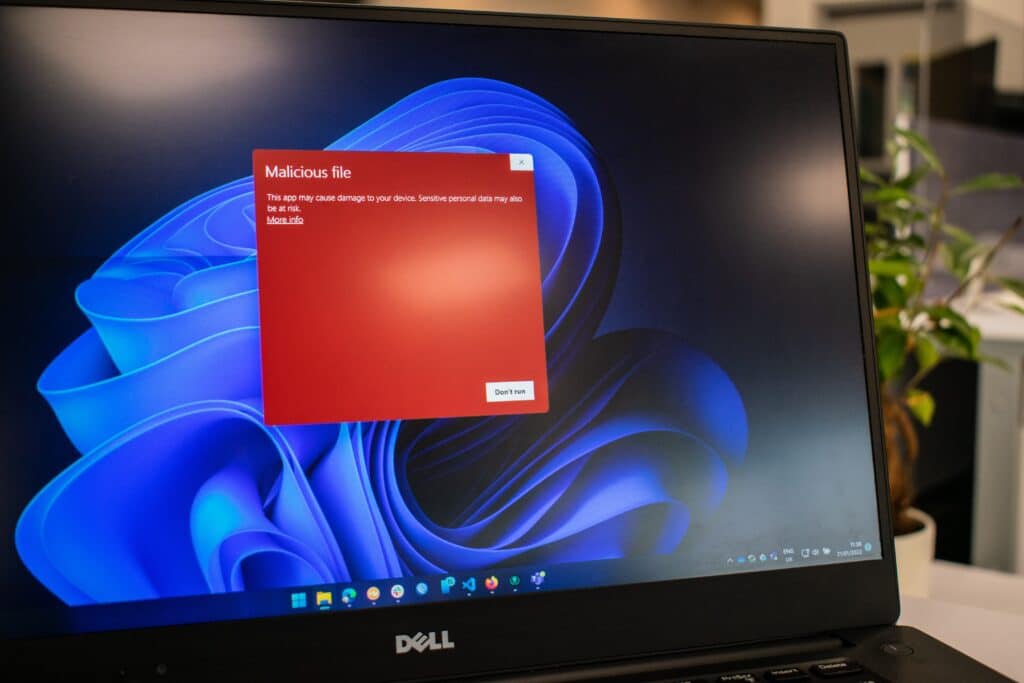

Why is User Application Hardening important?
The purpose of User Application Hardening is to create multiple layers of security to make it increasingly difficult for bad actors to comprise a User based application to compromise a user’s device. If one layer of security is breached, multiple security measures remain to protect the organisation’s computer systems.
The ACSC Essential Eight recommends hardening the configuration of User based applications that interact with the Internet (Web Browsers, Java, Flash, Adobe Acrobat Reader, etc).
User Application Hardening can be extended to remove the ability to use deprecated products (like Microsoft Internet Explorer 11) which are no longer supported by vendors and have known vulnerabilities.
The complexity of User Application hardening is that hardening rules need to be applied across multiple browsers, applications, and operating systems.
Introspectus Key Features
What's the solution?
Introspectus helps organisations maintain control over the IT security of their business environment by automatically testing the effectiveness of User Application Hardening.
Introspectus checks the configuration of each application referencing the configuration of Group Policy, Local Policy, and application-specific policies. This information is analysed and a maturity score is generated for the organisation.
Introspectus generates real-time reports on the Maturity Level of an organisation’s User Application Hardening Controls against ACSC’s Essential Eight Maturity Model and any possible threats to user accounts. It confirms that:
- User Application Hardening policies are effective.
- User Application Hardening is deployed to all endpoints and identifies any endpoints where the policies have not been implemented.
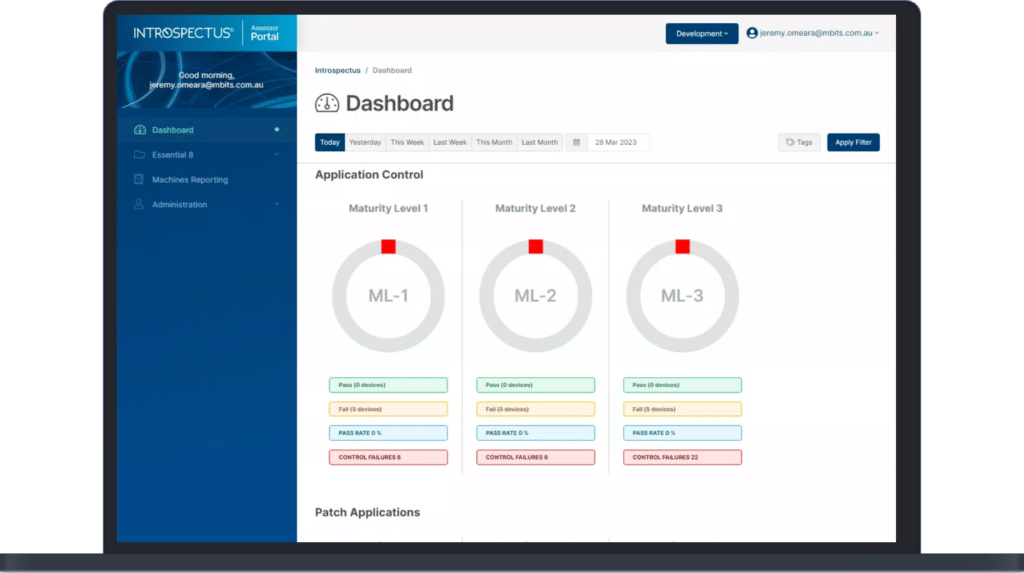
Automated Daily Tests
Introspectus automatically tests the effectiveness of User Application Hardening on all endpoints daily across multiple browsers, applications, and operating systems.
Identify Threats
Introspectus User Application Hardening controls and identifies any possible threats to user accounts.
Real-Time Reporting
Introspectus lets organisations confidently report to management that User Application Hardening is working effectively.