DISP Adopts the Essential Eight
Defence supply chains are a common target for state-sponsored cyber threats, espionage, and ransomware. The Defence Industry Security Program (DISP) seeks to ensure that suppliers to Defence are cyber-resilient, by implementing controls that endeavour to protect classified or sensitive information from compromise.
DISP members are now required to meet or exceed the Australian Signals Directorate (ASD) Essential Eight (E8) Mitigation Strategies at Maturity Level 2 across their ICT corporate systems.

Introspectus Assessor
Introspectus Assessor assists organisations aiming to achieve and maintain Maturity Level 2 across the Essential Eight; especially those preparing for, or already involved in, the Defence Industry Security Program (DISP).
| Capability | How Introspectus Assessor helps organisations achieve Maturity Level 2 |
|---|---|
| Guided Assessments | Map and measure against the E8, ISM, and DSPF |
| Evidence Collection | Organise compliance evidence in one place |
| Risk-Based Remediation | Prioritise 'what' to fix and 'when' |
| Executive Dashboards | Report status and progress to leadership |
| Automatic Continuous Testing | Removes human bias and error during assessments |
What is DISP?
The Defence Industry Security Program (DISP) is the framework used by the Department of Defence to ensure that industry partners can securely engage in Defence projects.
Industry entities who wish to apply for DISP membership are required to meet several eligibility criteria that are defined in the Defence Security Principles Framework (DSPF).
DISP Cyber Security Requirements
DISP Cyber Security Requirements includes the Essential Eight (E8) Maturity Model:
- A set of eight mitigation strategies identified by the Australian Cyber Security Centre (ACSC) as the most effective to prevent cyber-attacks.
- DISP participants must now implement the Essential Eight to Maturity Level 2 to maintain DISP membership.
Essential Eight Preventative Measures
The Essential Eight outlines a minimum set of preventative measures that organisations need to implement within their environment. Further, while the Essential Eight can help to mitigate the majority of cyberthreats, it will not mitigate all cyberthreats. Additional mitigation strategies and controls therefore need to be considered, including those from the Australian Government Information Security Manual (ISM).
Maturity Level 2 focuses on proactive controls, such as regular updates, and restricting access to provide protection against many moderate-level cyberthreats.

Essential Eight Maturity Level 2
The preventative measures required by Maturity Level 2 present a level of protection against moderate cyberthreats.
| Mitigation | Maturity Level 2 Description |
|---|---|
| Patch Applications | Security patches for internet-facing and high-risk apps (like browsers, PDF readers, Office) are applied within 2 weeks of release (or sooner if actively exploited). |
| Patch Operating Systems | Security patches for OS vulnerabilities are applied within 2 weeks, or sooner if exploited. Unsupported OS versions are not used in Production. |
| Multi-Factor Authentication (MFA) | MFA is enforced for remote access, privileged accounts, and key systems. This includes VPNs, cloud apps, and administrator access to servers and endpoints. |
| Restrict Administrative Privileges | Administrative rights are strictly limited to those who need them. Separate accounts for admin and user tasks are enforced. Regular reviews of privileges are performed. |
| Application Control | Application control is implemented on workstations and servers to block unauthorised executables (e.g., .exe, scripts) and software. Only approved applications can run. |
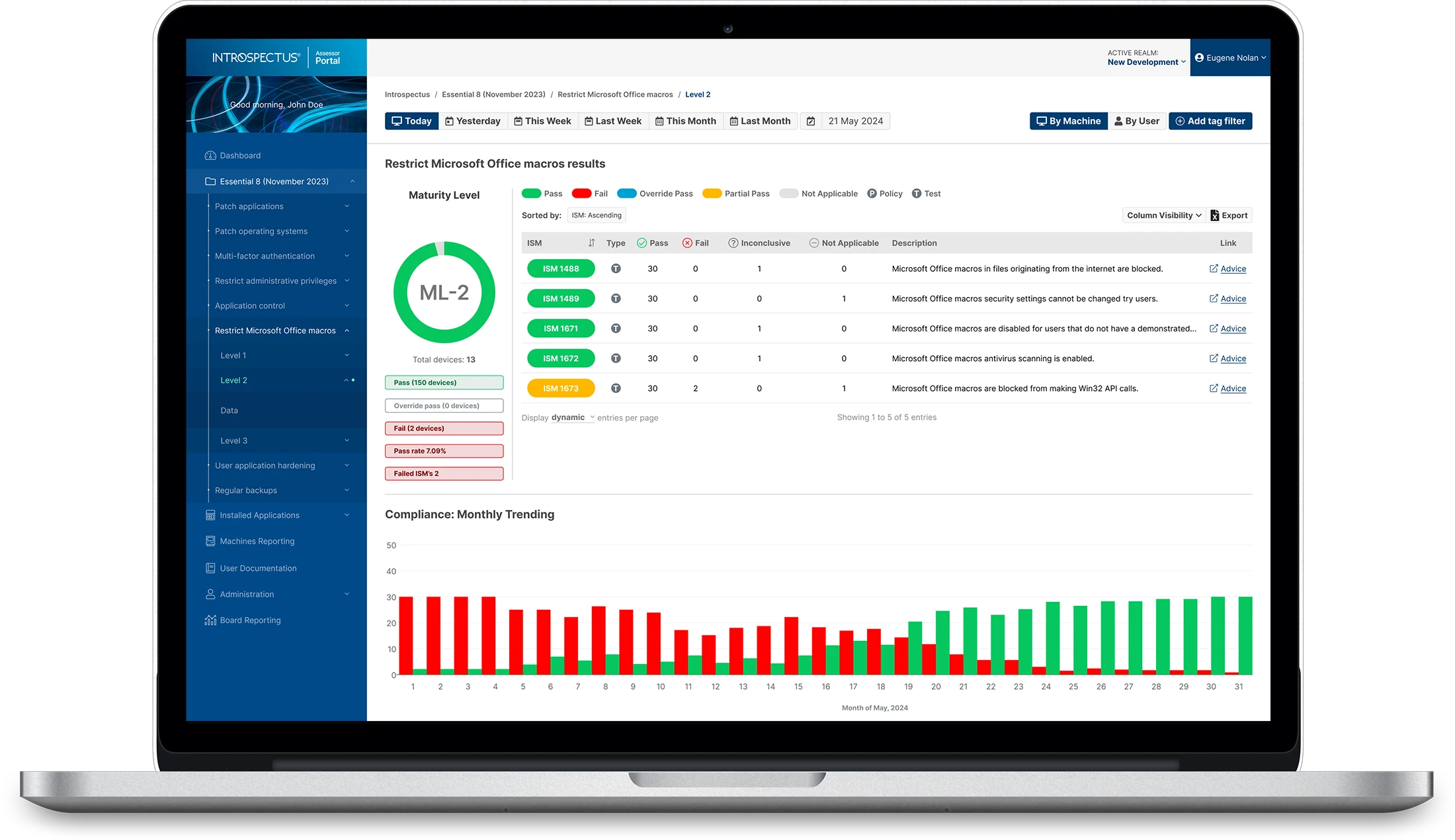
| Restrict Microsoft Office Macros | Macros are disabled by default. Only digitally signed macros from trusted sources are allowed. Execution is limited to trusted locations. |
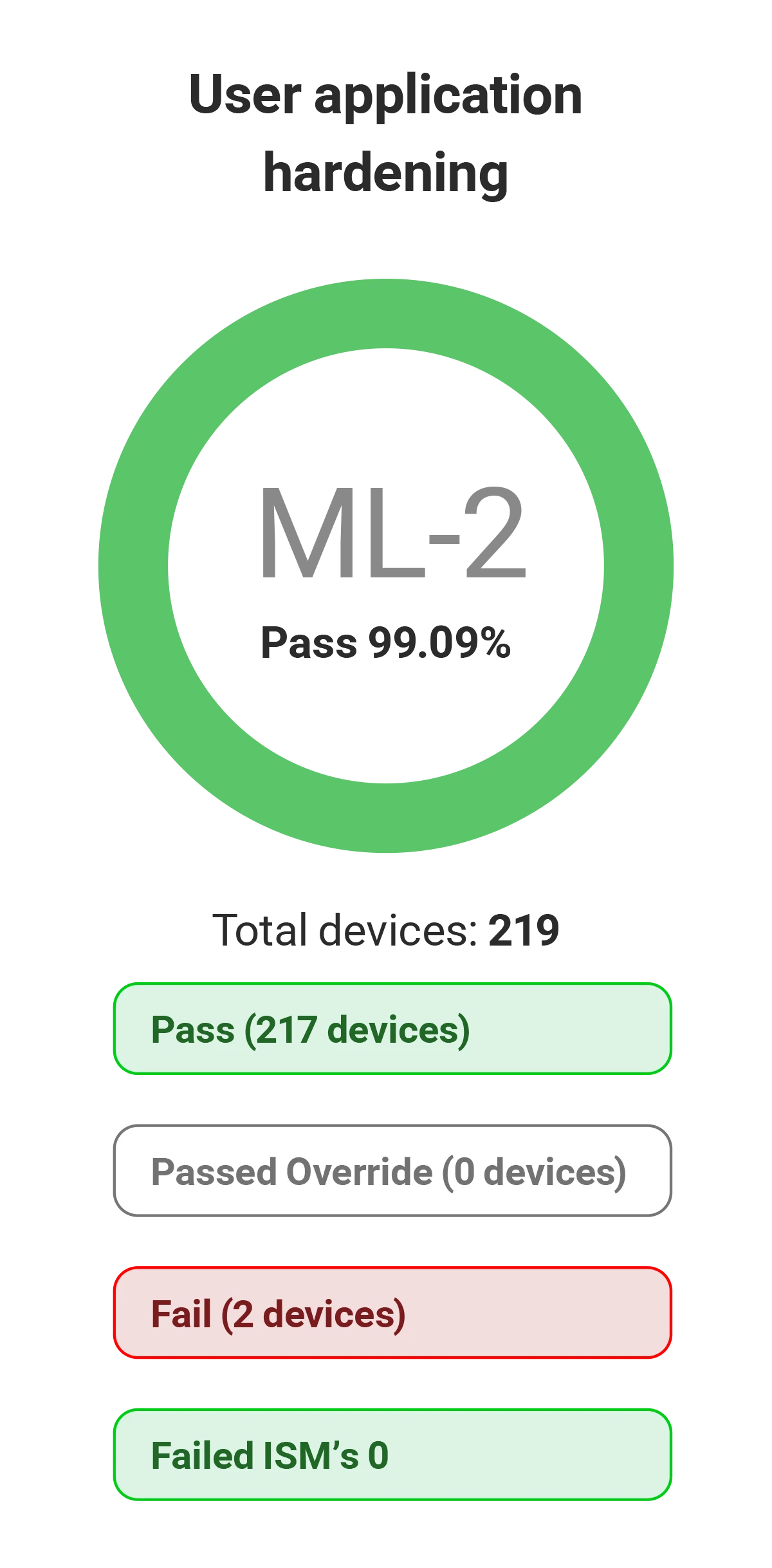
| User Application Hardening | Web browsers and document readers are configured to block Flash, ads, Java, and disable unnecessary features. Unsafe content types are not rendered. |
| Regular Backups | Regular Backups are performed daily, tested periodically, and stored in a segregated location (e.g., offline or immutable). Restoration procedures are proven to work. |
In the News
According to the ACSC report: ‘The Commonwealth Cyber Security Posture in 2024’, only 15% of government entities achieved overall Maturity Level 2 across the Essential Eight mitigation strategies in 2024, down from 25% in 2023. This 10-percentage point drop indicates that a significant number of entities have either regressed in their cyber security posture or have not kept pace with evolving threats and compliance requirements.
Maintaining cyber maturity requires an active, continuous approach. Without regular testing, ongoing control validation, and sustained staff awareness organisations risk drifting out of compliance and becoming vulnerable to avoidable cyberthreats such as ransomware and targeted intrusions.
